Unfortunately, attempts to steal data are oftem found in phishing attempts sent directly to our personal inboxes. Levels of sophistication can vary from attempt to attempt. In this phishing attempt, the email was sent from someone that claimed to be “iCloud.” A closer look at the sender’s email address sends red flags to the careful […]
Edge Computing
What is edge computing? Edge computing is when processes are performed locally on the “edge” of the network making the amount of long-distance communication limited and communication between devices happen more quickly. Instead of devices exclusively communicating with the cloud, they communicate with their own, local servers/computers first. This reduces the amount of data being […]
Recovery After a Disaster
Whether it’s a fire, a natural disaster, human error or cyberattack, it is important to respond to a disaster in the best way possible. Every hour of downtime is crucial to the recovery of a business. Business continuity plans exist to help get the business up and running as soon as possible after a disaster. […]
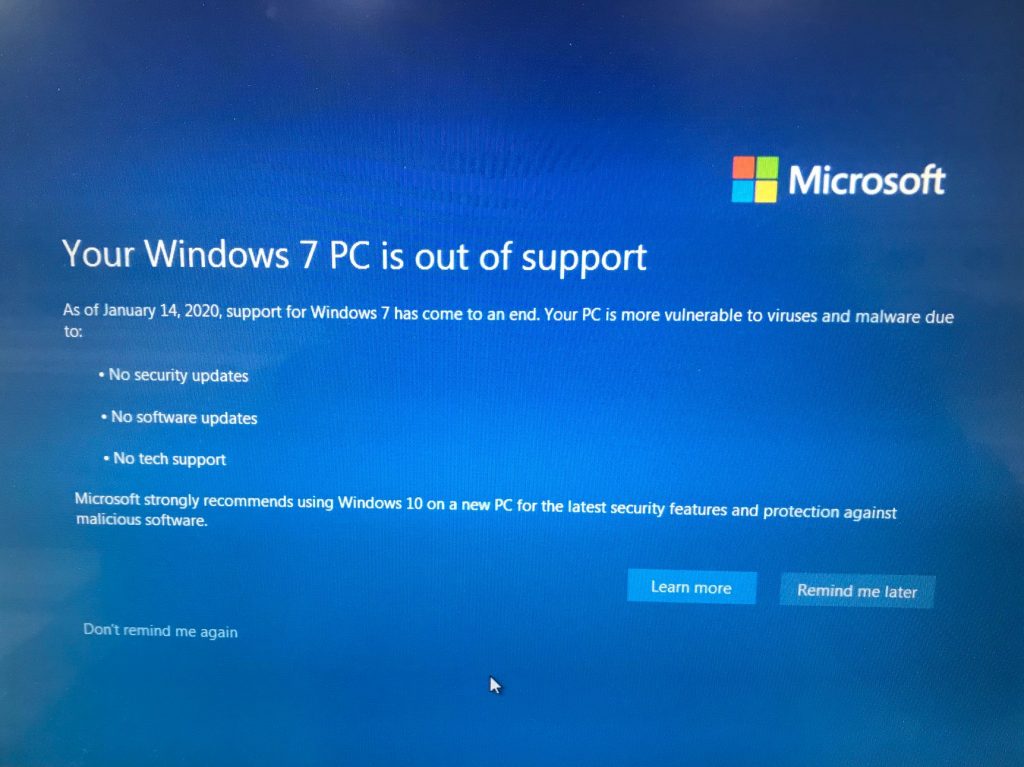
What should I do when I get this Windows 7 pop-up?
As of January 14, Windows 7 received its last round of security updates. The operating system was released in 2009 and has been a stable computing environment. The beloved operating system, however, is no longer able to support new technology- forcing its retire. If you’re seeing a pop-up on your machine informing you that your […]
Tips for Cleaning Up Your Computer
Little by little, your computer can get bogged down and operations may take a little longer than they did when the computer was new. Having a full or nearly full hard drive can cause your computer to slow down, making simple tasks take much longer to perform. The fairly simple task of cleaning your computer […]