Phish Fact #1
There are certain keywords that often pop up in the subject lines of emails with malicious intent. Watch out for these words and how they might be used.
Invoice
- Re: Invoice
- Missing Inv ####; From [Legitimate Business Name]
- INV ####
New
- New Message from ####
- New Scanned Fax Doc-Delivery for ####
- New Fax Transmission from ####
Message
- Message From ####
- You have a New Message
- Telephone Message for ####
Required
- Verification Required!
- Action Required: Expiration Notice on [business email address]
- [Action Required] Password Expire
- Attention Required. Support ID: ####
<Blank Subject>
Blank subject lines are often used by cybercriminals to help evade any automated security measures that are in place. The thought behind this is that if there isn’t any subject line, then the security technology can’t flag it for any phishing or spam keywords.
File
- You have a Google Drive File Shared
- [Name] sent you some files
- File- ####
- [Business Name] Sales Project Files and Request for Quote
Request
- [Business Name] SALES PROJECT FILES AND REQUEST FOR QUOTE
- [Business Name] – W-9 Form Request
- Your Service Request ####
- Request Notification: ####
Action
- Action Required: Expiration Notice on [business email address]
- Action Required: [Date]
- Action Required: Review Message sent on [Date]
- [Action Required] Password Expire
Document
- File Document ####
- [Name], You have received a new document in [Company system]
- Attn: [Name] – You have an important [Business name] designated Document
- Document For [business email address]
- View Attached Documents
- [Name] shared a document with you
Verification
- Verification Required!
eFax
- eFax from ID: ####
- eFax message from “[phone number]” – 2page(s), Caller-ID +[phone number]
VM
- VM from [phone number] to Ext. ### on Tuesday, May 4 2021
- VM From ***#### Received – for <[user name]> July 26, 2021
- ‘”””1 VMAIL RECEIVED on Monday, June 21, 2021 3:02:55 PM””
Source: https://expel.io/blog/top-phishing-keywords/
Phish Fact #2
Are there links or attachments contained within an email you just received? Follow these tips to identify if the email is safe to interact with.

Phish Fact #3
A new type of attack misuses Google Docs to spread malicious links. Here’s how:
Malicious hackers use the comment feature in Google Docs
Cybercriminals can send messages to just about any email address through commenting on a Google document/spreadsheet/presentation. It can be easy to fall for the trick, as the email is actually sent from Google so it may appear trustworthy.
All a fraudster needs to do is to create a Google document, spreadsheet, or presentation and add a comment tagging the target’s email address. Google will then automatically send a “helpful” email letting the user know that they have been mentioned in a comment. The email will include the comment along with any links (including malicious ones) as well as any links that may be contained in the actual Google document, spreadsheet, or presentation.
Phish Fact #4
At first glance, this email looks pretty inconspicuous. Upon close inspection though, it’s clear it’s a phishing email.
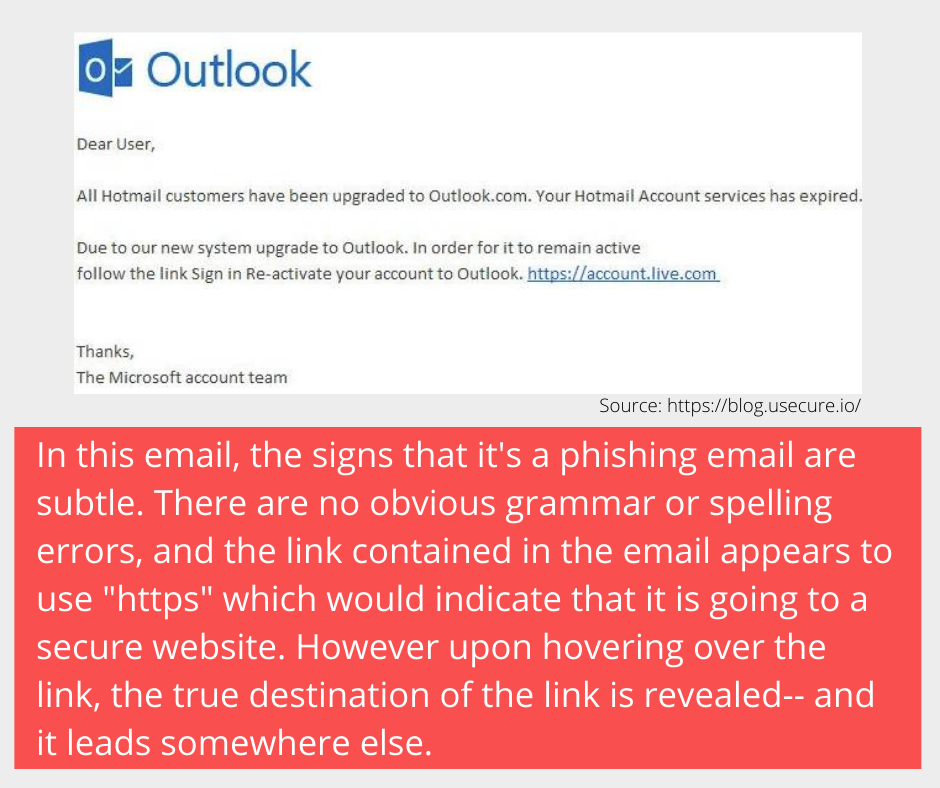
Phish Fact #5
There are a few approaches that are used commonly by cybercriminals to get the information they are seeking from the victim.
Social Engineering
Social engineering is often used as a weapon against the victim. It is common for phishers to attempt to pull on the emotional heartstrings of victims in order to get the victim to do what they want them to do. Commonly targeted emotions include: hope, curiosity, and necessity. Scam emails may include messages of the promise of money, include wording that gets you to wonder what happens next and/or instill a sense of urgency that action needs to be taken.
Current Event-Themed
Another tactic that phishers will use is to exploit human vulnerabilities and anxieties with current events. For example, COVID-19-related phishing emails were very popular and successful at the peak of the pandemic. In addition, tax-related phishing emails commonly occur during tax season.
Spear Phishing Attacks
When a phishing attack is targeted at one person or a small group of people, this is known as a spear phishing attack. This type of attack generally requires a little more knowledge about the target and can include personal details to make the email seem more legitimate. This type of attack is also less likely to be picked up by phishing filters than the common phishing attempt.
Not all phishing emails are caught by email filters. This is why teaching employees how to spot a phishing email will offer further protection from falling victim to a phishing attack.
Phish Fact #6
Understanding how a phishing email is built can help you spot one when it shows up in your inbox. Here’s a step-by-step of an attacker’s approach to creating a phishing email.
- Pick your target
- The more information you have about your target, the easier it is to craft an email that the target will interact with. The audience you pick may be broad or specific. For example, your email could target customers of a particular bank, or you could target a certain role within an organization or even a specific individual.
- Choose emotional triggers (select your bait)
- Attackers will always choose an emotional trigger to get a victim to fall for their scams. There are three emotions that phishers will commonly use to trap their victim:
- Curiosity: Humans are naturally inquisitive and phishers will abuse this by making you want to know more.
- Hope: Phishers also commonly instill hope in their messages to lure victims. This can range from general messages about unexpected prize wins and dating opportunities to job offers, pay increases, and more.
- Necessity: Phishers will often make you believe that you must act now in order to avoid a negative consequence.
- Attackers will always choose an emotional trigger to get a victim to fall for their scams. There are three emotions that phishers will commonly use to trap their victim:
- Build the email (bait the hook)
- In building the email, phishers will often attempt to cloud the victim’s judgement by using at least one of the emotional triggers. This makes it more likely that a victim will react in the way the phisher wants without thinking about it first. The action could be as simple as clicking a link, or more complex like initiating a wire transfer.
- Send the email (cast the line)
- The last step is to send the email to the target(s). In order to do this, the phisher will need to create a somewhat believable email address for the email to come from. Many phishers will do this simply by using a generic service like Gmail. A savvy user may catch his right away though. To be even more tricky, they can instead purchase a domain name that looks similar to the one they want to mimic.
- Another, even trickier-to-catch approach, would be for an attacker to compromise an email account that belongs to the legitimate source and use it to send a scam message. This is commonly known as Business Email Compromise (BEC).
Phish Fact #7
Phishing Impersonation is another tactic that cybercriminals will use to gain the trust of the victim. Phishing Impersonation attacks will usually pose as emails from a well-known company like Microsoft or WeTransfer. The goal of these attacks is to trick the victim into believing the email is legitimately from the well-known company and get them to click on a phishing link. According to the report 49% of all socially engineered threats are phishing impersonation attacks.
While hackers are able to impersonate any brand/company they want, there are definitely certain brands that get impersonated more than others. There is a tendency to expect communication from our favorite or most-used brands, and that makes people more likely to trust any communication that comes from them. Because of this natural human tendency, it is more common for hackers to impersonate popular brands/companies. According to the report from Barracuda, Microsoft, WeTransfer, and DHL have remained the top three brands used in phishing impersonation attacks since 2019.
Phish Fact #8
Google can help protect your data with data that it collects. Google’s Safe Browsing and Gmail spam filters automatically scan billions of emails, webpages, and apps for threats. This helps paint the clearest, most up-to-date picture of the current phishing landscape so the security systems can block things it perceives as threats.
If a user clicks on a link to a phishing site in the Gmail app for Android or iOS, a warning will show if that site has been flagged by Safe Browsing. Safe Browsing will also warn Gmail users if it detects suspicious email attachments. Safe Browsing helps protect more than 3 billion devices from phishing, across Google and beyond. It hunts and flags malicious extensions in the Chrome Web Store, helps block malicious ads, helps power Google Play Protect, and more. It will also show red warnings about websites it considers to be dangerous and insecure. This is featured in multiple browsers– Chrome, Firefox, Safari– and across many different platforms, including iOS and Android.
