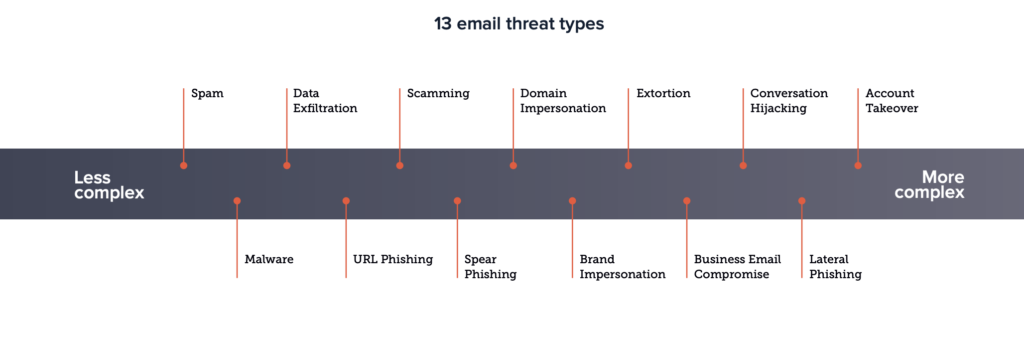
A recent report from Barracuda only goes to show how important it is to implement phish training for employees in the workplace. Cybercriminals are constantly changing their tactics to better evade automatic detection filters as well as better trick an unknowing victim. Due to this, the complexity of email threats is increasing. As said in the report from Barracuda, there are 13 threat types faced by organizations today. These range from high-volume, less-complex attacks like spam or malware to more complex and targeted attacks like business email compromise attacks and impersonation attacks.
Phishing Impersonation
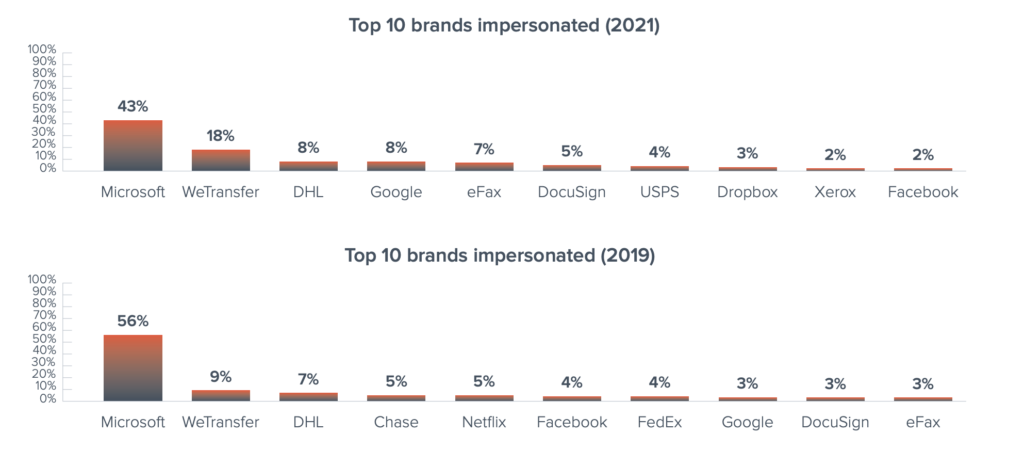
Phishing Impersonation attacks will usually pose as emails from a well-known company like Microsoft or WeTransfer. The goal of these attacks is to trick the victim into believing the email is legitimately from the well-known company and get them to click on a phishing link. According to the report, 49% of all socially engineered threats are phishing impersonation attacks.
While hackers are able to impersonate any brand/company they want, there are definitely certain brands that get impersonated more than others. There is a tendency to expect communication from our favorite or most-used brands, and that makes people more likely to trust any communication that comes from them. Because of this natural human tendency, it is more common for hackers to impersonate popular brands/companies. According to the report from Barracuda, Microsoft, WeTransfer, and DHL have remained the top three brands used in phishing impersonation attacks since 2019.
Business Email Compromise
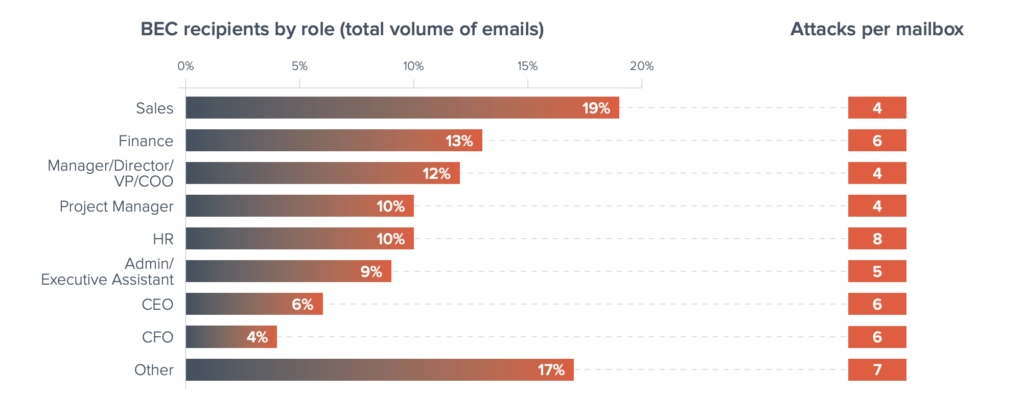
Business Email Compromise, or BEC attacks usually involve impersonating an individual. The threat actor will impersonate either someone inside or outside of an organization, usually an executive employee, and request wire transfers, gift cards, or donations to bogus charities. This past year, BEC attacks made up 10% of all socially engineered attacks. This type of attack will target basically any industry: education, healthcare, commercial, travel-organizations, and more.
Members of finance are usually popular targets for BEC attacks. It was reported that in the past year CFOs received around 4% of all BEC attacks. Finance departments as a whole received 13% of all BEC attacks. Another popular target of BEC attacks are people who’s roles are sales-related. There are often a large number of sales people in an organizations, so the percentage of total BEC emails that go to sales departments, may appear a little skewed. It was reported that 19% of BEC attack emails went to people who have sales roles. However the number of attacks was less than that of people who have finance roles. On average, there were four attacks per inbox for people in sales roles, and six attacks per inbox for people in finance roles.
Extortion
According to the report, extortion attacks only make up 2% of the total amount of phishing attacks from the past year. Most of these attacks were sextortion email threats, where hackers demand a ransom with the threat that they will expose sensitive or embarrassing content if not paid. In extortion, ransom payments are usually demanded in bitcoin so the payment is difficult to trace.
Scamming
Last year, scamming attacks represented 39% of all social engineering attacks. Scamming attacks are generally a less-targeted attack where threat actors cast a wide net with many different types of scams. Because of this, these threats cost victims hundreds of millions of dollars. Their techniques usually rely on piggybacking on current events. For example, this past year, scams that claimed they were looking for investments in fraudulent coronavirus treatments/vaccines were popular.

Spear-Phishing Attacks
Spear-phishing attacks are targeted phishing attacks. Instead of a wide net being cast like in scamming attacks, spear-phishing attackers will spend time researching their victims to build an attack that they are more likely to fall for. Oftentimes, the type and amount of information the target(s) has on social media sites will help attackers create an accurate picture of the individual(s) and discover their weak spots.
How can you protect your business and users against an attack?
Technology
- Take advantage of artificial intelligence. Scammers are adapting email tactics to bypass gateways and spam filters, so it’s critical to have a solution in place that detects and protects against spear-phishing attacks, including business email compromise, impersonation, and extortion attacks. Deploy purpose-built technology that doesn’t solely rely on looking for malicious links or attachments. Using machine learning to analyze normal communication patterns within your organization allows the solution to spot anomalies that may indicate an attack.
- Deploy account-takeover protection. Many spear-phishing attacks originate from compromised accounts; be sure scammers aren’t using your organization as a base camp to launch these attacks. Deploy technology that uses artificial intelligence to recognize when accounts have been compromised and that remediates in real time by alerting users and removing malicious emails sent from compromised accounts.
- Implement DMARC authentication and reporting. Domain spoofing is one of the most common techniques used in impersonation attacks. DMARC authentication and enforcement can help stop domain spoofing and brand hijacking, while DMARC reporting and analysis helps organizations accurately set enforcement.
People
- Train staffers to recognize and report attacks. Educate users about spear-phishing attacks by making it a part of security-awareness training. Ensure staffers can recognize these attacks, understand their fraudulent nature, and know how to report them. Use phishing simulation for emails, voicemail, and SMS to train users to identify cyberattacks, test the effectiveness of your training, and evaluate the users most vulnerable to attacks.
- Review internal policies. Help employees avoid making costly mistakes by creating guidelines that put procedures in place to confirm requests that come in by email, including making wire transfers and buying gift cards.
- Maximize data-loss prevention. Use the right combination of technologies and business policies to ensure emails with confidential, personally identifiable, and other sensitive information are blocked and never leave the company.
Source: Barracuda Spear Phishing Report
