Many of the cyber threats that impact and target business entities had previously
Below is a list of the threats we have seen on K-12 networks this year, and tips for preparing your staff for future cyber threats. The list is overwhelming and ever-growing. Please do not hesitate to reach out if you have questions about protecting your users from any of these scenarios.
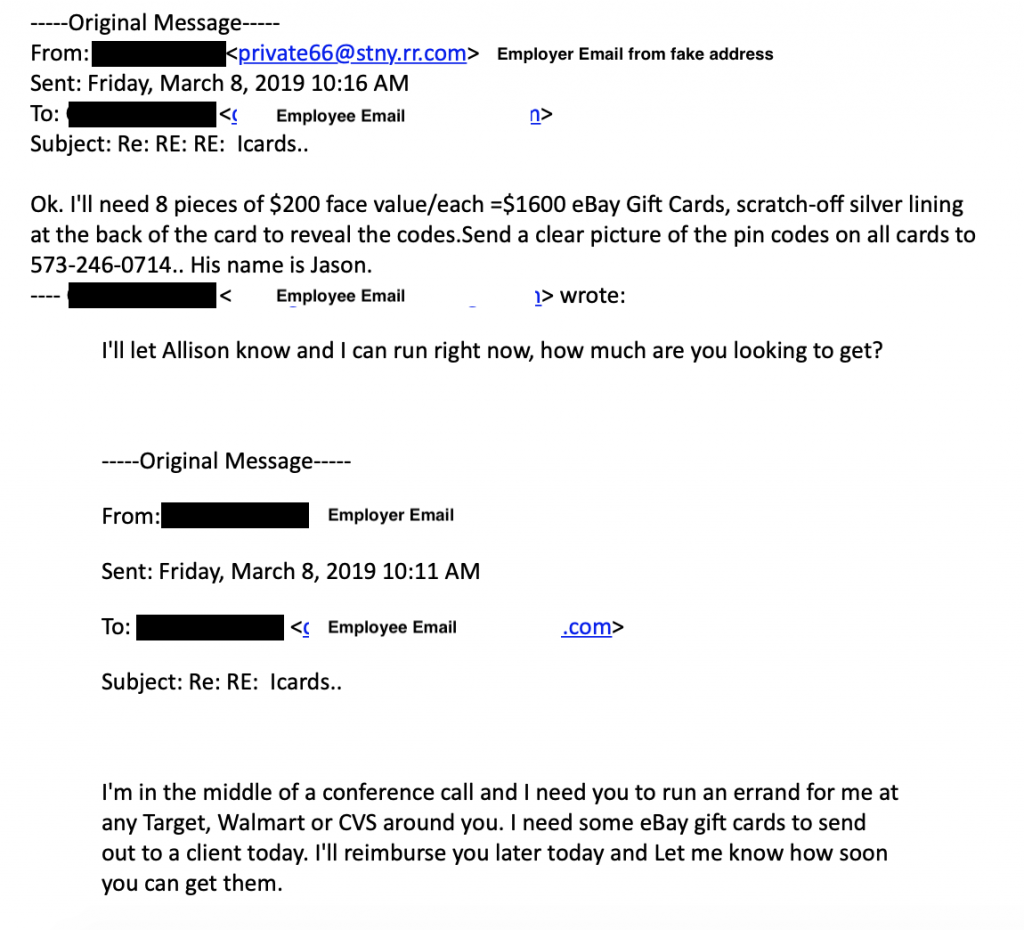
Fake Boss Emails
The email below is a sample of what we call a “Fake Boss Email”, although many varieties exist. In these emails, the attacker will present themselves as a boss or coworker requesting a money transfer, gift cards, or other financial changes. The email will say the name of an actual coworker, but a closer look at the address will show you that it is a spoofed email and not actually from your domain. A closer read will also usually reveal some grammar, spelling or word choice oddities as well.
It is always a good idea to check with the person requesting the purchase or financial change in-person or via phone call – replying to the email is not acceptable because your reply is typically sent back to the attacker instead of your coworker.
Teach staff how to look for signs that an email is spoofed, and develop/review policies for processing financial requests. Anyone that has power and permissions to transfer funds, route ACH payments for payroll or process bills payable/receivable should consider additional training on spotting spoofed emails and know your policy for verifying financial requests.
You can also setup warnings in your Google Apps Domain to alert users that an email came from outside your organization. Read instructions for adding an external sender notification and Adding enhanced phishing and malware notifications and let us know if you need help adding any settings or policies to your email domain.
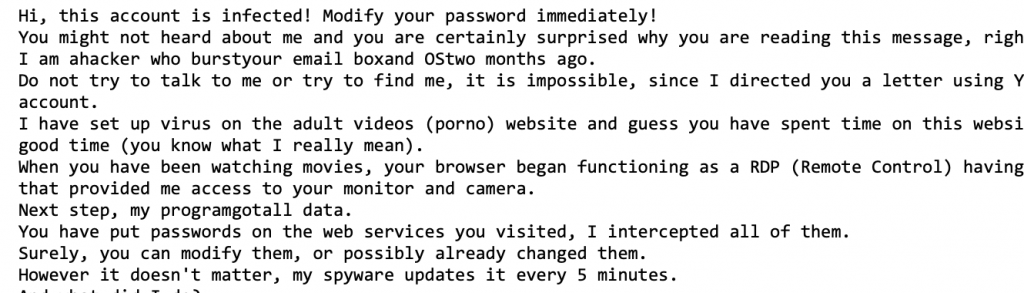
Sextortion Emails
These emails are especially frightening because they generally contain actual passwords that you have used in the past and claim to have access to your computer along with proof of unseemly browsing history.
The likely explanation behind this type of email is that one of your passwords was at one point compromised from a breached site: Target, Experian, DropBox, and MyFitnessPal are all sites that have lost usernames, passwords, and email addresses in the past few years.
If a specific password was referenced in the email and it is a password that you currently use, change it and stop using it on all sites/logins. Although these emails indicate the hacker has access to your computer, we have not seen this to be true.
Key Logger Viruses
Viruses can come from a variety of sources and present in a variety of ways. Viruses can be downloaded unknowingly from hacked websites, from clicking an email attachment, or from opening Microsoft Office documents that are infected. An especially problematic type of virus is a key logger.
If a staff member’s computer is compromised with a key logger virus, then anything the staff member types on their computer could also be compromised. We have seen this type of attack reach to personal Amazon shopping accounts, personal bank/credit card accounts and even social media credentials. Key logger viruses can also harvest credentials and information that help them reach other computers and servers on your network.
A solid endpoint protection or antivirus software is the best way to contain these types of threats.
Ransomware
Ransomware cases have decreased this year, but it is very much still a threat. Ransomware is most often initiated through an email. These emails are typically phishing in nature, and may lead you to believe that they are from FedEx, UPS, Amazon, etc. and are trying to resolve an issue with your order.
Some ransomware emails have also impersonated shared documents and document sharing sites like DropBox, Google Drive, etc.
Whenever you receive an email with a link or attachment, you should always look at the sender address area before proceeding. Check to see if the sender name (Leslie Althoff) matches the sender address (Leslie@infrastructuretech.net) If I appear to send you an email from my name, but the address is 22bogus@gmail.com, you can delete the email and know that someone has spoofed my address.
If you receive an email that contains an unexpected attachment or unexpected link, hover over the item before clicking. If the address that appears in the preview box is the address you expected it to be and the rest of the email looks legitimate, you can proceed with clicking. If you hover over a link that says “Google Doc has been shared with you” but the hover information shows a .php file, you should delete the email. When in doubt check directly with the sender and ask if they meant to share that specific document or link with you.
Some of the same email settings mentioned above in the “Fake Boss Emails” section will help alert your users to ransomware. Training users how to spot scammy emails is also an important part of avoiding ransomware and viruses.
View more in-depth tips for checking emails for threats.
This Is Microsoft Calling
Phone calls from hackers pretending to be Microsoft or other service providers can present a double-whammy: calls could come into a school office or a staff member’s home. If a staff member accepts a call from “Microsoft” at school, they may follow given instructions to help the caller gain access to a computer/network or visit a specific website. The hacker could then deploy a virus, steal information, etc. If the caller accessed a machine with server access, other machines on the network could also be compromised.
If staff members (and even students!) take school computers home and receive a “Microsoft” call at home, allowing the hacker to access their school machine at home could later impact the school network. When the school computer comes back to work/class on Monday and checks into the network, any malicious files installed by the hackers while the computer was at home could then spread to other school machines on the school network.
It is important to train your staff to not interact with these types of phones calls: Microsoft will not call to provide technical support for your computer. If you receive a pop-up telling you to call an 800 number because you have a virus, this is also fake, Make sure staff know who your IT provider is if you use a third-party provider and what methods they use to communicate with staff and establish remote connections.
Learn more about browser hijacks – the pop-ups that appear and tell you that you have a virus, have downloaded a sketchy file, etc.
Phishing & Social Engineering Assessment
Did you know that ITS can provide a phishing and/or social engineering assessment for your District? Both of these assessments target a specified number of staff members, and present a series of emails that look realistic but follow typical phishing patterns. The behaviors of the email recipients are recorded and reported: Did they click? Did they give-up credentials? Did they delete? Schools can then provide targeted training for users that illustrate a need for more email security training.
Social Engineering assessments involve a series of phone calls, wherein a third-party attempts to gather information from a school employee over the phone. Information given to callers over the phone could violate FERPA and/or HIPAA, and could also inadvertently give out information that impacts school safety, network security and more.
