A new week brings a new series of targeted email threats. Round one is a twist on the recent sextortion campaigns, but places clients in a more difficult situation. Many of the emails contain physical threats: bombs brought into buildings or mercenaries waiting outside with acid. Just like the round of webcam sextortion emails that cycled recently, payment in bitcoin is demanded to escape the threatened situation.
Round two is a series of emails from “executives” within your company requesting gift card purchases for company gifts.
I Know It’s You, Bob
Last week, we fielded two helpdesk calls with the latter type of phishing email, likely also integrating some social engineering components. The emails claimed to be from company executives, and were sent to other employees within the company. In the emails, the executive asked the employees to purchase gift cards for him to use as corporate Christmas gifts. The executive also asked for them to remove the privacy strip and report the redemption code back to him for use online. In both cases, the employees saw the emails as odd, and responded to the executive for clarification. The executive responded back, in a somewhat personal manner and repeated the request, as the replies were going to the spoofed address instead of the executive’s actual email address.
Eventually, both companies contacted ITS to take a look, and we were able to help them confirm that the emails were targeted phishing. Screenshots below show how the address was spoofed and not actually from the company executive. However, when the employee replied, they only saw the sender name and not the sender address, creating the illusion that the executive was sending/receiving these requests.
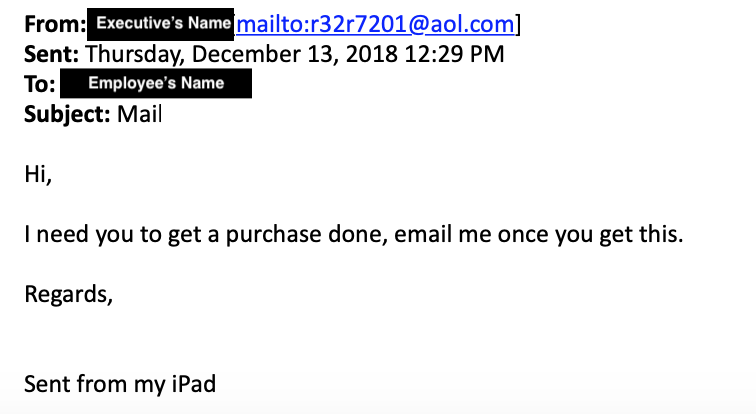
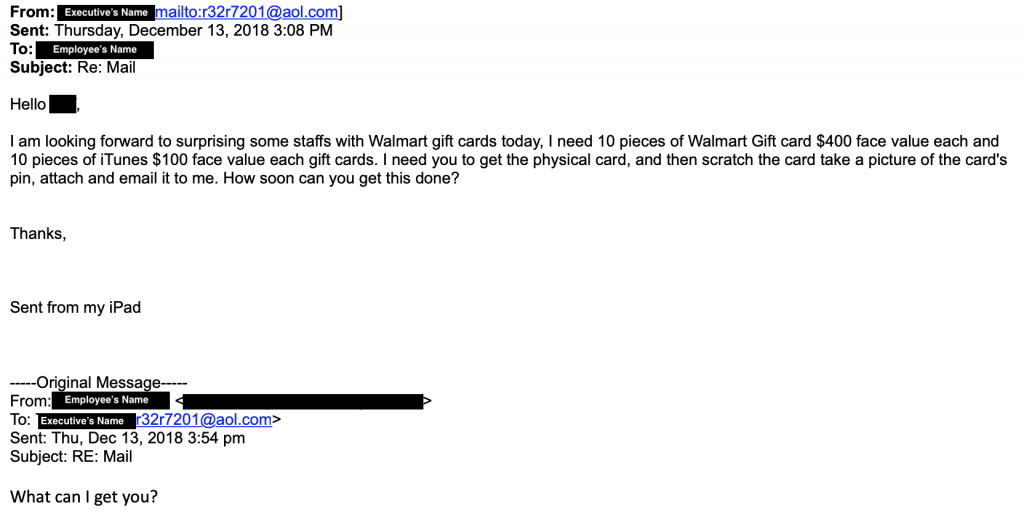
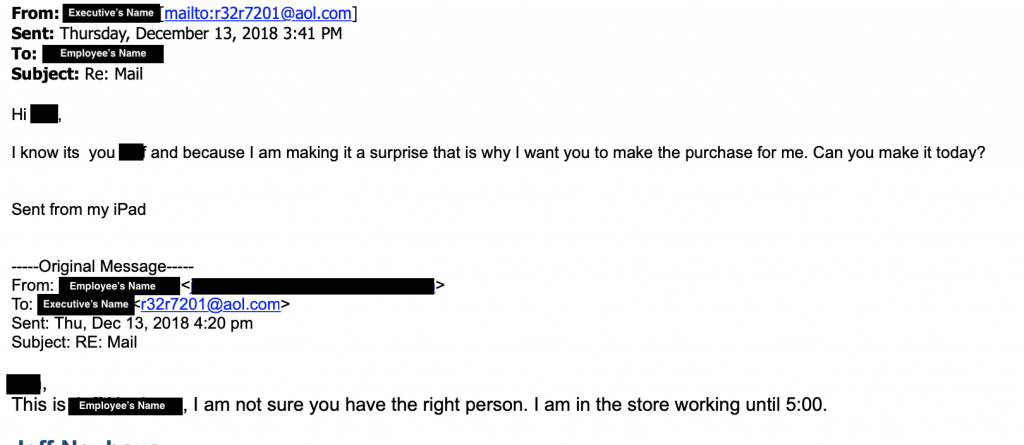
How Is My Information Found?
When clients see these phishing attempts come through, they often wonder how their information is found. How do scammers know who the president is, who handles the books, or who the most likely candidate for buying gift cards would be? The information could have come from your website, where staff, titles and roles are shared to be helpful and inviting. Small details about your company may have also come from a targeted phone call to your business.
Just today when I was reading reports on this latest round of email threats, our incoming phone line rolled over to me. I answered, and fielded a call asking for a specific co-worker. As the co-worker was in a meeting, I asked if I could take a message or offer assistance. The caller proceeded to give his name and company, which was not something I recognized. The caller asked for the email address of the co-worker, which I declined to share. Being a good gatekeeper on the phone is a great way to limit social engineering via telephone. If people call and ask for details about your business, your staff and operations, or ask for specific email addresses, etc., make sure that you know who the caller is and why they need that information. A caller that is able to collect useful pieces of information about your business and your staff is one who may also use/share that data later for nefarious purposes.
How Do I Mitigate Risk?
- If an email request seems odd or out-of-character, personally contact the sender via phone or face-to-face to ask about the requested transaction. Replying via email is not always a safe choice, as you may be replying to the scammer’s email address and not the address of your coworker.
- Consider the information on your website: what is necessary for clients and prospective clients? What information is too much information and could aid scammers?
- Train phone handlers to be good gate-keepers; don’t let them give out email addresses, cell phone numbers, titles or names unless they can validate the request for information.
- Develop a policy for any financial requests. Make sure that your bank/bankers also have a security protocol for money transfer requests.
